Privacy enhancing computation is a technique that ensures sensitive information is kept confidential when it is used by multiple parties to collaborate on tasks.
If two parties are working on a project that requires them both to share their data – but they don’t want to reveal the private information within – they can use PEC as a safeguard to collaborate without sharing the secure details.
PEC uses mathematical techniques that allow all parties to perform calculations on the data without explicitly sharing the information. It ensures the collaboration remains honest and that no security protocols have been breached.
According to technology research and consulting company Gartner, by 2025, 50% of large businesses will adopt privacy-enhancing computation to process data in untrusted climates and multiparty data analytics use cases.
![privacy enhancing computation]()
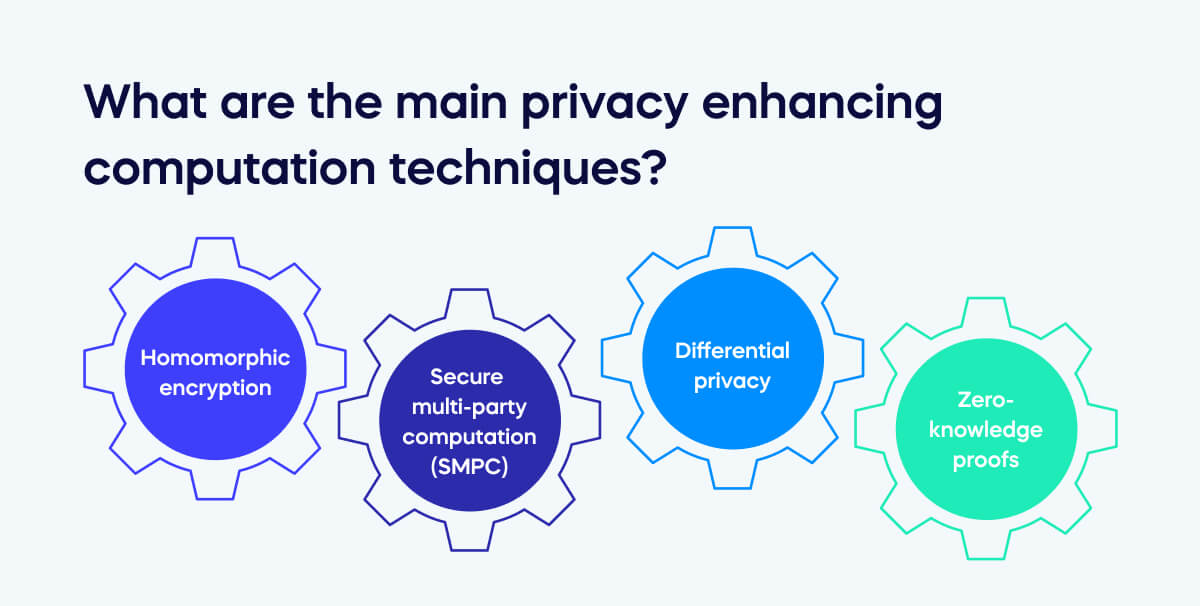
What are the main privacy enhancing computation techniques?
Several techniques can be used to protect data privacy within the context of privacy enhancing computation. Here are the four most popular approaches.
Homomorphic encryption
This method allows for computations to be performed on encrypted data without decryption. As the data remains encrypted throughout the process, its privacy is ensured. There are different types of homomorphic encryption, such as partially and fully homomorphic.
Secure multi-party computation (SMPC)
SMPC allows for multiple parties to collectively work on a solution to a specific problem without revealing the private data they have contributed for analysis.
Using cryptographic protocols and algorithms, SMPC allows participants to input their data into a shared system without revealing what it is. Instead, the system performs the calculation while keeping individual contributions hidden; all participants can only see the final result.
Differential privacy
This privacy protection concept adds ‘random noise’* to information to protect individual data. The benefit of this method is that useful insights can still be drawn from the details. For example, if there was a database of people’s salaries and a business wanted to find out the average salary without revealing a specific person’s salary, a little ‘random noise’ would be added to the result to make it impossible for the exact salary of any individual in the database to be figured out.
* The concept of adding random or unpredictable data to the real data so that the overall aggregate information is not significantly changed, but it is more difficult to determine individual values.
Zero-knowledge proofs
This approach allows for parties to prove they have the correct information to perform a calculation or access data without revealing the information itself. For example, employees may show their employer they know their password without revealing it.
In this instance, the employee performs a number of steps proving their knowledge of the password and presents the result to the employer. The employer will check the results by performing the verification steps. If the employee’s result matches what the employer would get by following the steps, then the employer is assured that the employee knows their password.
![What are the main privacy enhancing computation techniques]()
Which business sectors use privacy enhancing computation?
Healthcare – Diabetes data analysis
Healthcare organizations need to share sensitive data for specific tasks or projects. For example, two hospitals may want to work together to find treatments for diabetes, and the project may involve using patient records with highly confidential health information.
The records would be encrypted, and then PEC techniques such as SMPC would be used to perform joint computations on the encrypted data to find answers such as the average age of patients with diabetes without revealing individual ages.
Finance – Loan risk assessment
Financial services can use PEC to protect sensitive information during secure transactions and analysis. If a bank wants to streamline a loan approval process while ensuring customer financial information is kept private, they can use a PEC technique like SMPC to calculate the encrypted data.
They can figure out information such as the debt-to-income ratio for each applicant to assess their creditworthiness, making informed decisions without accessing the raw financial data of applicants.
Smart home technology – thermostat recommendations
A smart home technology company may want to analyze temperature data to improve their thermostat performance without compromising user privacy. In this instance, they could use homomorphic encryption.
The data would be available from the smart thermostats, but it is sensitive information. Therefore, the data is encrypted using this PEC method before it is sent to the company’s central server for analysis.
![privacy enhancing computation]()
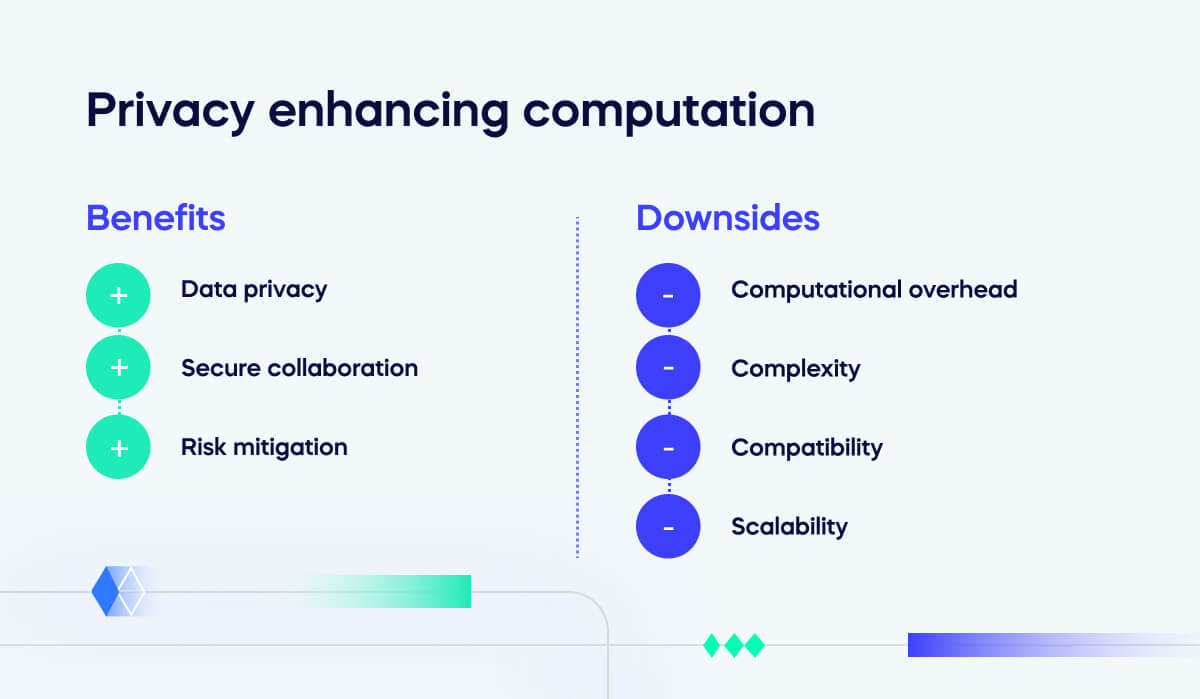
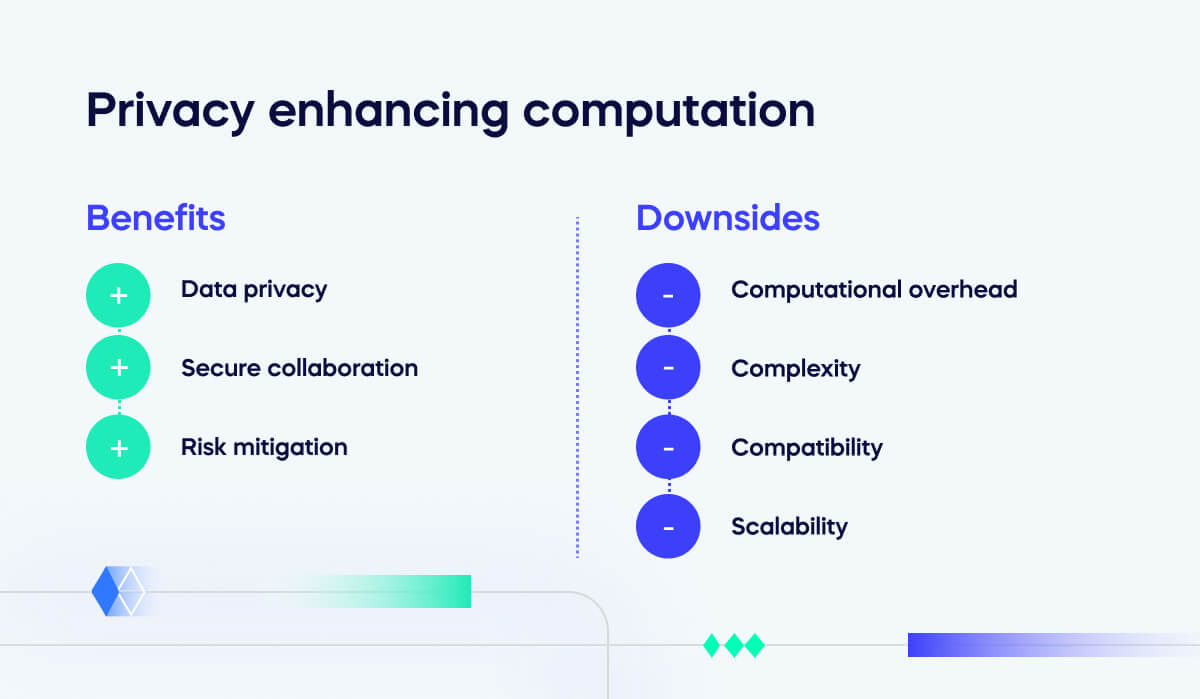
Benefits of privacy enhancing computation
Businesses enjoy a variety of benefits with PEC:
Data privacy
PEC allows organizations to protect sensitive data while obtaining the necessary information. They will remain compliant with data protection regulations and maintain the trust of their users or customers.
Secure collaboration
Multiple parties can collaborate on projects, research, and data analysis without exposing their private information.
Risk mitigation
Organizations will comply with privacy regulations such as GDPR, HIPAA, and CCPA. They will be safeguarding sensitive data and avoiding costly fines or legal complications.
Privacy Enhancing Computation (PEC) serves as a crucial component in Integrated Risk Management (IRM) by providing advanced data protection during processing, thereby enhancing an organization’s ability to manage and mitigate data privacy and security risks.
Downsides of privacy enhancing computation
PEC can have some downsides which are worth considering:
Computational overhead
More computing power is required to process data while it’s encrypted, which can slow down operations and increase costs.
Complexity
PEC techniques require specialized cryptographic knowledge and expertise. Any mistakes made in implementation could lead to vulnerabilities or privacy breaches.
Compatibility
These approaches may not be compatible with all systems and software. Integration can be particularly challenging with legacy systems. Information technology services may need to be updated before PECs can be used.
Scalability
PEC methods may not scale well if large datasets or a high volume of users are accessing the data at once. Managing the computational load can introduce new challenges for companies.
Updated: October 17, 2023