Everyone talks about how essential cloud technology investments are, but who stops to think about security? The US government does, but don’t worry, it is in a way that is supportive of every business. They created the handy FedRAMP framework to ensure legal compliance and support with cloud data security.
Because a government-wide program like FedRAMP can be confusing and take excessive time to get authorized, we have created a guide to digital FedRAMP adoption.
This guide will allow you to be compliant, secure, and effective with cloud data storage. You will then avoid the average cost of a data breach of USD 4.35 million, according to IBM research in the US in 2022, caused by weak security. Your company may be able to avoid this waste with digital FedRAMP adoption.
To show you how this article will explore FedRAMP digital adoption through the following topics:
- What is FedRAMP?
- What is digital FedRAMP adoption?
- Why is digital FedRAMP adoption essential to business?
- What are the benefits of FedRAMP?
- What are the steps to effective digital FedRAMP adoption using a DAP?
What is FedRAMP?
FedRAMP, the Federal Risk and Authorization Management Program, was established in 2011 and based on federally funded research to help reduce federal risk in the government tech stack.
It helps central government agencies standardize a cost-effective, risk-centered approach to cloud services like computers and phones to operate securely in large enterprises to protect federal and corporate data.
A good summary is shown in the video below by the US General Services Administration, briefly describing what existed before FedRAMP.
A FedRAMP Overview: Introduction
However, the staff uses many similar terms in the same sentence as FedRAMP, and it can be confusing to interpret them all. Let’s get familiar with some of them below to ensure you optimize your use of FedRAMP, beginning with SOC 2.
What is digital FedRAMP adoption?

Digital FedRAMP adoption is the process of your staff learning how to use FedRAMP within their daily processes. This process will be more straightforward for some and more difficult for others, depending on their experience with security software and techniques.
How you adopt FedRAMP depends on whether you are doing so via the agency or JAB (Joint Authorization Board) route. For both routes, there are four main steps:
- Select authorization path (Agency or JAB)
- Preparation
- Authorization
- Continuous monitoring
Why is digital FedRAMP adoption essential to business?
FedRAMP adoption is essential to business in many ways, as it is a legal requirement if your organization uses cloud services, it makes your organization more credible and helps accelerate mission success for your digital transformation.
Legality
FedRAMP authorization is required. Using cloud-based technology in the US government must meet the FedRAMP standards to protect the government’s investments in technology and information, which amount to billions of dollars annually.
Credibility
FedRAMP authorization provides credibility. The process of getting authorized by FedRAMP is rigorous. It involves a three-step evaluation procedure. The first step is a security assessment, where agencies must comply with standardized controls and standards. Subject matter experts and third-party evaluators assess these standards.
FedRAMP Accelerates Digital Transformation
FedRAMP authorization accelerates digital transformation. FedRAMP is a program across the entire government that encourages using secure cloud services by outlining specific security and risk assessment requirements that cloud technologies must meet.
Our digital adoption platform is the only FedRAMP-approved DAP on the market. It leverages proprietary technology to improve your organization’s visibility to an organization’s CIO (chief information officer) and business leaders. It optimizes user experience and employee productivity using in-app guidance and personalized learning.
Once your organization meets all the requirements, the FedRAMP program will grant a security authorization. It is important to note that your organization must follow an ongoing assessment and authorization plan to remain compliant after authorization.
What are the benefits of FedRAMP adoption?
There are many benefits to FedRAMP adoption, as can be seen in the list below, such as helping to avoid duplications and errors:
- Successful FedRAMP digital adoption helps to avoid repeating tasks, discrepancies, and wasted expenses and encourages better adaptability to change for your staff.
- A FedRAMP digital adoption initiative creates a collaboration between the public and private sectors to encourage innovation and enhance the development of secure information technologies.
- The federal government can speed up the use of cloud computing by setting clear standards and processes for security authorizations and allowing agencies to use these authorizations on a government-wide level.
It is essential to know these benefits to ensure you get the most out of your FedRAMP digital adoption following confirmation of authorization.
What are the steps to effective digital FedRAMP adoption using a DAP?
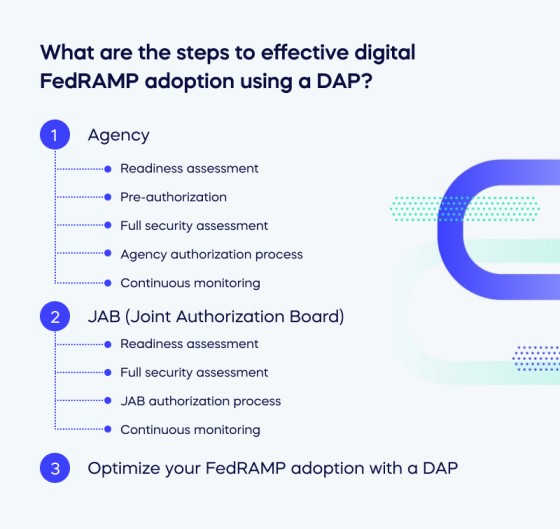
There are two ways to follow the steps to effective digital FedRAMP adoption using a DAP: Agency or JAB. Let’s begin with the agency route.
Agency
Agency sponsorship means that one agency wants to use your solution and will help you get approved by the FedRAMP process. The agency route is the most common way to get approval and happens 70% of the time. Any government department, agency, or organization can purchase cloud solutions and be part of this conversation.
A DAP helps at this stage as it can support employee training on the differences between agency and JAB entry routes to inform the best decision for your organization.
Readiness assessment
The FedRAMP Readiness Assessment is a crucial step in the authorization process that enables completing an assessment within six months as they approach FedRAMP-ready status. Before starting the authorization process, it checks if a CSP has the necessary system capabilities.
Completing the process can take much longer than usual without proper preparation. However, a DAP can help train staff on all information needed to streamline this process.
Pre-authorization
After receiving the Readiness Assessment Report, the PMO assesses whether or not a vendor meets the FedRAMP “Ready” standards. The process involves working alongside the CSP and 3PAO to analyze the capabilities of the CSP. If the vendor successfully meets the FedRAMP Ready requirements, they can maintain the status for up to a year.
There are many FedRAMP requirements, and they can be challenging to understand and remember. A DAP can assist in this process using in-app guidance, which helps learners explore new apps as they learn.
Full security assessment
To start the authorization process, a CSP must first conduct a comprehensive security assessment, as mandated by JAB. Doing so involves including the SSP, SAP, and SAR in the security authorization review from the outset. This approach allows for a more integrated and comprehensive system evaluation rather than a partial assessment.
The CSP and 3PAO are responsible for the security assessment, leading to the complete security authorization package. When scheduling testing, they should refer to FedRAMP’s Timeliness and Accuracy of Testing document, which specifies the acceptable timeframes for assessment evidence of new and existing Agency authorized systems.
This document aims to prevent CSPs from undergoing an early full assessment, which would result in outdated assessment evidence and them to carry out a new evaluation. A DAP assists your staff in understanding the legal language of the entire security assessment with personalized learning offered as part of the DAP learning package.
Agency authorization process
In this phase, the agency team will conduct a review of the CSO authorization package, including the System Security Plan (SSP) with attachments, Security Assessment Plan (SAP), Security Assessment Report (SAR), and POA&M for quality and risk assessment.
The review aims to verify that the authorization package is clear and precise in representing the CSO’s security posture, thus aiding the Agency Authorizing Official (AO) in making a well-informed, risk-based authorization decision.
The authorization package review process can appear complicated at first glance, but a DAP can simplify and streamline this process.
Continuous monitoring
After your organization receives agency authorization has been granted, you will receive continuous monitoring to ensure it complies with the FedRAMP standards. These standards change over time, and a DAP can help you keep track of these changes if it is connected to FedRAMP to facilitate automatic updates to training features.
JAB (Joint Authorization Board)
The JAB is a group that ensures organizations follow all rules for FedRAMP. It includes people from three federal organizations: the Department of Defense, General Services Administration, and Department of Homeland Security. The JAB works with the FedRAMP PMO to make sure everything runs smoothly.
A DAP can assist with all the process points when applying for FedRAMP authorization through the JAB route in the same ways described above.
Readiness assessment
The readiness assessment for JAB applications is the same as described above in the agency section.
Full security assessment
To start the authorization process, a CSP must first conduct a comprehensive security assessment, as mandated by JAB. Doing so involves including the SSP, SAP, and SAR in the security authorization review from the outset. This approach allows for a more integrated and comprehensive system evaluation rather than a partial assessment.
The CSP and 3PAO are responsible for the security assessment, leading to the complete security authorization package. When scheduling testing, they should refer to FedRAMP’s Timeliness and Accuracy of Testing document, which specifies the acceptable timeframes for assessment evidence of new and existing Agency authorized systems.
The purpose of this document is to prevent CSPs from undergoing an early full assessment, which would result in outdated assessment evidence and the need for them to carry out a new evaluation.
JAB authorization process
The JAB Authorization Process has four key steps, each with exact timeframes and decision points. Doing so creates clear expectations of the process and helps FedRAMP and CSPs make yes or no decisions, allowing for progress in the authorization process within the given time constraints.
FedRAMP Accelerated is a new system the federal government has initiated to streamline the process of FedRAMP authorization.
The four steps in the JAB Authorization Process are:
- Kick-Off (one week): The CSP, 3PAO, JAB, and PMO will have a series of detailed, in-person sessions to review the system’s capabilities, boundaries, services thoroughly, and any identified risks from the 3PAO’s security assessment.
- The JAB Review process will take around three to four weeks to complete. It will involve thoroughly examining all the security package documents by JAB reviewers. The aim is to identify potential risks, deficiencies, or areas requiring more clarification.
- During the remediation period, which could take up to twelve weeks, but the estimate is three weeks, the CSP and 3PAO will improve system functionality, testing, and documentation based on JAB comments received during their review.
- The JAB takes four weeks to review and approve the CSP and 3PAO remediation work and ensure they address all comments. This step is necessary to confirm the CSP’s provisional authorization.
Continuous monitoring
The FedRAMP Continuous Monitoring Strategy Guide explains that ConMon requires the CSP to regularly monitor their security controls, assess them, and prove that the security of its service offering remains acceptable.
Optimize your FedRAMP adoption with a DAP
Now that you know how to get FedRAMP authorization and the benefits it can bring your organization, why wait? Streamline your cloud security protocols with this rapid digital adoption process using digital adoption solutions today.
FedRAMP certification offers an excellent opportunity for those looking for improved digital transformation and costs savings from cloud services. Don’t miss out on the security enhancements and options available with FedRAMP authorization – get started today and enjoy better cloud security for years to come.
FAQs
What is the difference between FedRAMP and FISMA?
FISMA was a law that didn’t mention cloud technology. The government was worried about the safety of using cloud technology and followed stringent rules. FedRAMP created a plan to ensure cloud technology is safe and secure for government departments to work with cloud technology.
What is the difference between FedRAMP and RMF?
The federal government workforce has two authorization processes: FedRAMP and RMF. Federal agencies use RMF to obtain authorization for their systems and protocols, while FedRAMP is specifically for cloud service providers.
What is the difference between FedRAMP and CMMC?
The main difference between FedRamp and CMMC is that FedRamp is mainly used to verify the security of public cloud services for lasting government collaborations.
On the other hand, CMMC aims to demonstrate the current state of security compliance within an organization using a tiered hygiene approach (Levels 1-5), ranging from basic hygiene to advanced proactive hygiene.


