In today’s digital age, shadow IT is prevalent. But it goes beyond staff using dangerous apps in the shadows that could compromise an entire enterprise’s security system.
The reality is that today’s shadow IT activities often stem from employees seeking solutions due to a lack of adequate tools for their work. This situation frequently arises from ineffective digital change management within the organization.
An insightful approach to shadow IT involves developing a strategy that not only addresses these unofficial practices but also supports employees instead of penalizing them. This strategy fosters an environment marked by transparency, openness, and strong communication.
The number of employees using unauthorized apps is high, with a reported 41% doing so in 2023. You cannot ignore this issue and must treat the problem sensitively and with balance if you want employees to follow policy.
To help you build a secure and balanced shadow IT strategy, we will explore the following topics:
- How to implement a shadow IT strategy
- The benefits of shadow IT
- The risks of shadow IT
6 steps for implementing an effective shadow IT strategy
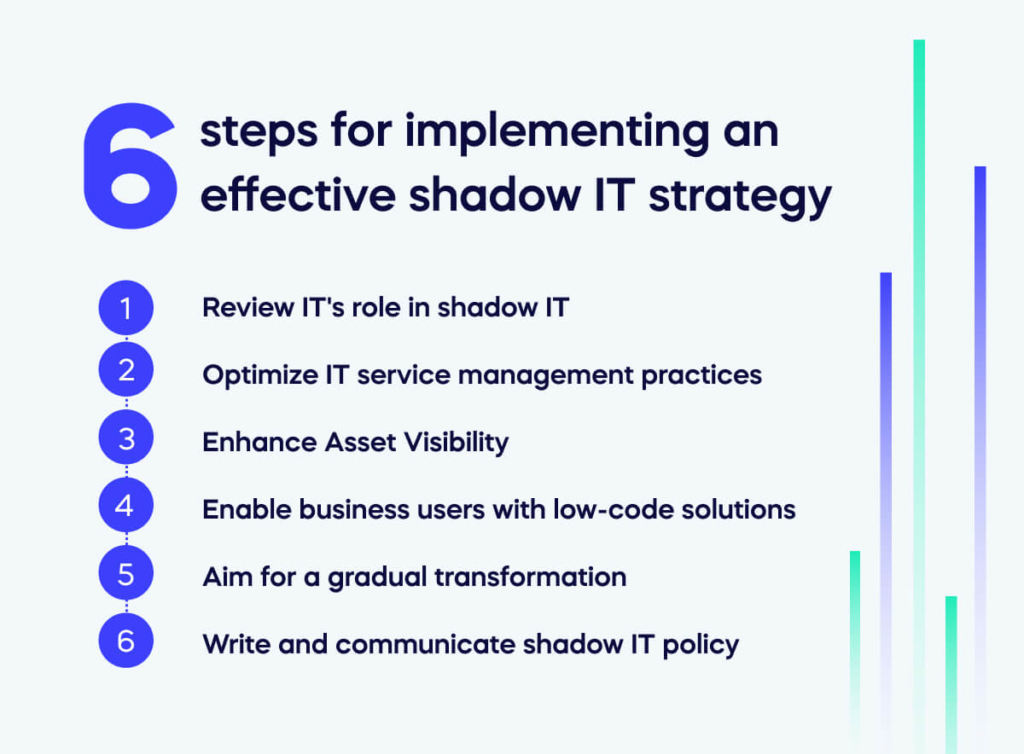
Implement these six steps to create a safe and balanced shadow IT strategy that will be actively embraced and adhered to by your employees.
- Review IT’s role in shadow IT
When addressing the issue of shadow IT, it’s essential to consider the role of IT in its proliferation.
Is IT slow to review and approve technology needs, or does it disregard employee perspectives and needs in favor of other tools or vendors?
Disharmony between IT and employees can lead to shadow IT, as dissatisfied employees seek alternatives independently.
Therefore, before implementing new policies, it’s crucial to assess areas for IT improvement and how to protect corporate data through authorized IT systems.
Drafting new rules won’t address the core issue of utilizing technology to effectively meet employees’ needs for achieving company goals.
- Optimize IT service management practices
IT Service Management (ITSM) is concerned with the end-to-end delivery of IT services to end-users. Its core job is to ensure smooth infrastructure operations, timely provisioning of new resources, and service/help desk support.
Although ITSM is an essential function, it’s frequently not acknowledged.
Over 58% of ITSM practitioners surveyed by Information Week in 2022 didn’t have an ITSM framework. Many also lacked self-service portals for users and effective IT service desk processes, which resulted in poor service levels.
Slow response times, rigid policies, and low quality of provided solutions by the ITSM function exasperate shadow IT.
If your marketing team urgently requires a new landing page, waiting two weeks for approval of a new SaaS app might not be feasible. Instead, they may go ahead with using an unsanctioned product.
Aim to align your IT department’s capabilities with the staff’s needs, starting with acknowledging shadow IT presence.
Instead of punishing users, explain the meaning of shadow IT to them and ask them to volunteer any information on such apps. Analyze the in-use software and bring the appropriate tools into the company’s security perimeter.
The next step is creating better workflows for requesting new software licenses, product features, or customizations.
Set up a standardized request template for business users and lean approval workflow. Make a couple of people accountable for monitoring and responding to this stream.
Finally, create a company-wide app ownership structure, which assigns different software to teams/departments.
Ensure all employees understand which tools are available and how to use them. Automate employee onboarding, data privileges sharing, and offboarding for users.
- Enhance Asset Visibility
The average company has 30% more exposed assets than its asset management programs have identified.
The first task to combat this is to create a detailed asset inventory, giving all assets a digital asset identity and documenting all elements within your tech stack, such as:
- Virtual machines (VMs).
- Local business apps.
- Integrated development environments.
- SaaS products.
- Cloud and on-premises storage.
- Miscellaneous hosts and APIs.
An asset management assessment serves the dual purpose of identifying unsanctioned apps on your network and consolidating IT spending. You’d likely be surprised by the number of abandoned, redundant, and outdated products you’re still paying for.
Such an audit also helps you improve your cybersecurity posture. With a sweeping scan, you can identify:
- Outdated versions of software or firmware in use.
- Designation and security status of various APIs.
- Number of open ports for different systems.
- Unknown hostnames and IP addresses.
Then, implement the necessary measures to tighten your security and shadow IT monitoring measures.
Leverage application mapping tools and network monitoring products to obtain visibility into your assets. Modern solutions cover all endpoints in on-premises, hybrid, and cloud environments.
- Enable business users with low-code solutions
Indeed, business users feel increasingly frustrated with legacy technologies preventing them from completing their tasks. So when they see a better app, they’ll use it without considering the shadow IT risks.
Low-code solutions can be an excellent alternative to haphazard app adoption and complex software modernization projects.
Providing users access to low-code tools can reduce the itch to use unauthorized products.
- Aim for a gradual transformation
You can’t win the battle against shadow IT in a day, especially when this practice has been unchecked for quite some time.
To achieve this goal, Microsoft ranked the team’s current maturity and designed a roadmap for the laggers to reach the optimal standards.
Combine all the technology and process-level improvements at the IT side with proactive employee outreach and training on security risks to achieve the highest impact.
- Write and communicate shadow IT policy
The final and most resource-heavy step is formulating and communicating a shadow IT policy. Doing so will cement all the previous steps, ensuring employees know their importance and carry them out long-term.
What to include in your shadow IT policy
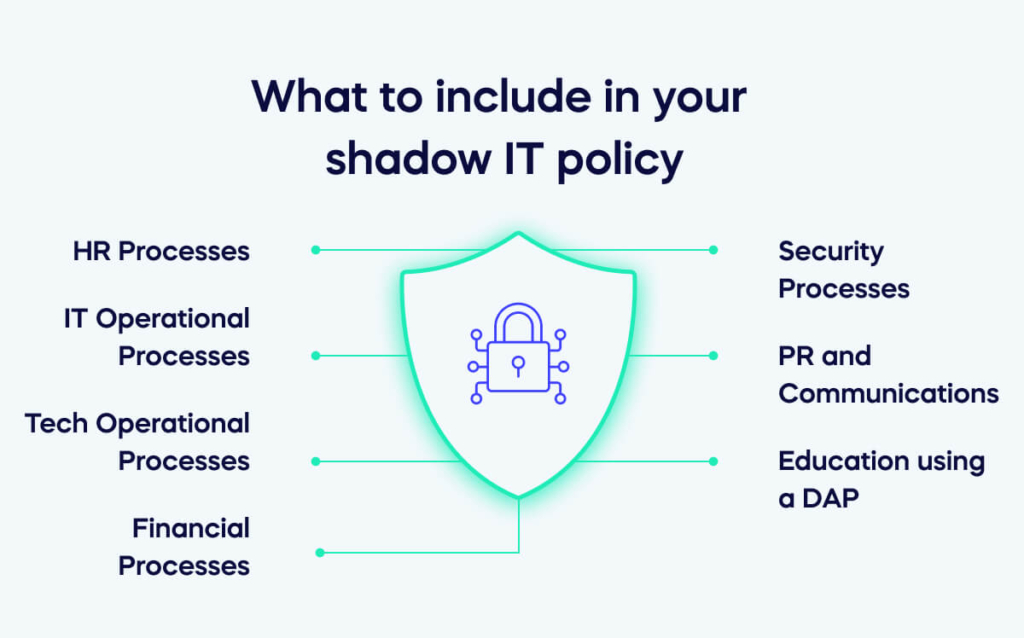
Creating a shadow IT policy is a significant undertaking, requiring the entire organization’s collective input to provide expertise for each element of the policy.
HR Processes
This section of your policy should be crafted in collaboration with the HR department and cover aspects such as managing employees who violate your shadow IT policy.
IT Operational Processes
Your policy should outline the processes for ongoing shadow IT discovery, disaster recovery procedures, and how IT will handle corporate data and security breaches resulting from cyber attacks or other means. You can also include the IT procurement process within this.
Tech Operational Processes
It is vital to address the processes for IT audits and approvals of new technology, dismantling shadow IT when necessary, and proactively managing license renewals.
Financial Processes
The IT team should collaborate with the Accounting department to review the financial implications of Shadow IT, identify potential areas of noncompliance, and address insurance concerns.
Security Processes
Since security is a crucial concern, your policy should thoroughly cover this area, including measures for shadow IT discovery, who can access company data, what actions could pose security risks, and mitigation.
Create a security checklist to guide how IT audits and evaluates any technology’s security.
PR and Communications
To prepare for a security event, it’s essential to collaborate with the Marketing, PR, and Communications departments to ensure their readiness to address the media, the company, and any impacted partners or customers.
Education using a DAP
It is crucial to incorporate a dedicated section in your shadow IT policy that outlines a process and schedule for continuous education to ensure ongoing employee education on Shadow IT and security. A digital adoption platform (DAP) is the best way to achieve this.
Another effective method for managing Shadow IT with employees is to implement a “freedom within limits” policy, which allows employees some flexibility while setting boundaries and guidelines.
It is crucial to understand the underlying needs driving Shadow IT usage within your organization and conduct IT audits to evaluate each technology.
Staff can use a DAP as they work and don’t need managerial input, saving resources. Additionally, it can create a catalog of pre-vetted options for employees, providing them with approved alternatives.
Throughout this process, it is essential to consider and communicate the context and reasons behind each IT decision, making employees feel valued and understood.
The benefits of shadow IT
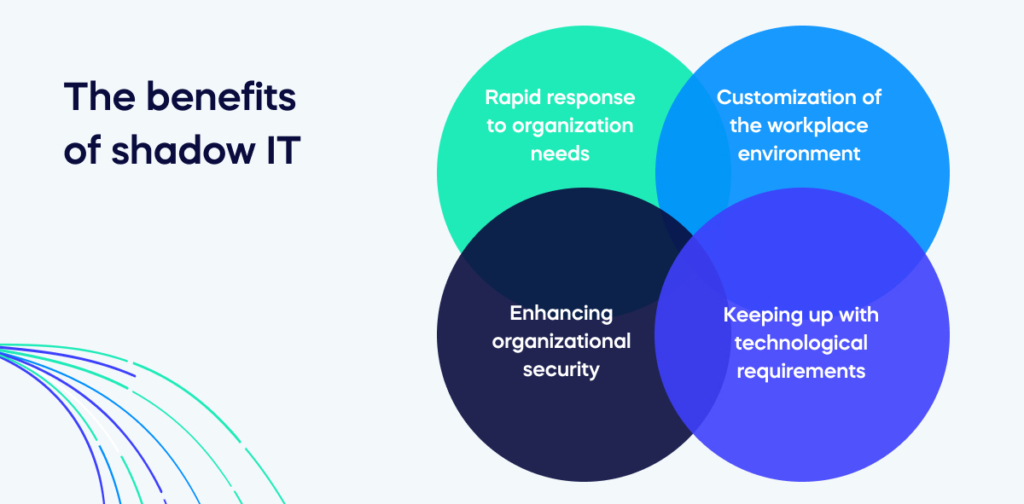
Leaders often perceive shadow IT negatively, yet employees engage in these practices for reasons that can be beneficial, as illustrated by the following four key advantages:
- Rapid response to organization needs
Shadow IT will enable employees to address their needs using their technology and resources, bypassing the need for IT department approval.
One example is that during a technological change, a team member may download new software in advance to prepare for its use on the company network.
Doing so enables organizations to leverage employee insights to find the most suitable IT solutions for their teams.
- Customization of the workplace environment
Shadow IT enables employees to personalize their workspace using their IT resources.
This action may include downloading software that enhances workflow, increasing productivity and employee retention as employees are satisfied they are achieving their goals and completing tasks the way they choose.
- Keeping up with technological requirements
Shadow IT enables employees to download and install necessary software without IT department approval.
This feature is particularly useful when organizations require specific software or hardware to stay compliant in their industry.
For example, if a bank’s software is incompatible with new ATMs, shadow IT allows team members to upgrade the operating system without delay.
- Enhancing organizational security
Shadow IT can enhance security within an organization by allowing users to update their technology with newer versions with updated security features.
For instance, if a company uses advanced spam filters on its email server but doesn’t enforce other spam protection methods throughout the network, team members downloading the latest spam protection software can be seen as positive examples of shadow IT.
The risks of shadow IT
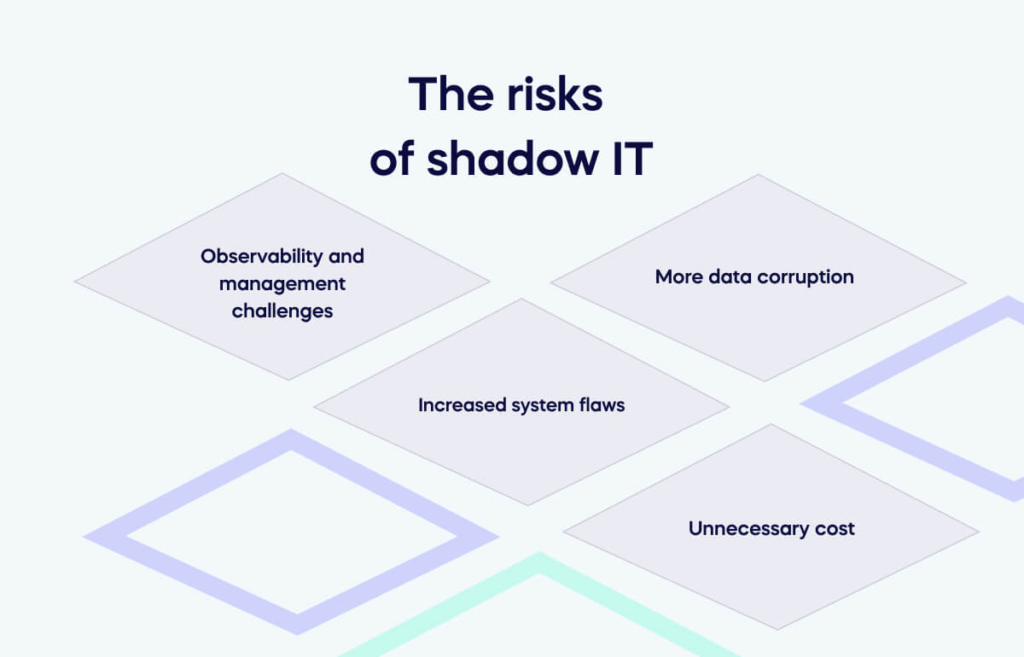
Despite the advantages of shadow IT, there are also risks. The four most common of which you can find below. Awareness of these risks can help you avoid them through proactive planning and communication.
- Observability and management challenges
Shadow IT refers to using digital services or devices not approved by the IT department, posing cybersecurity risks as the organization’s security measures do not protect them.
However, it can provide faster access to resources and improve communication and collaboration.
- More data corruption
Another difficulty with shadow IT is that company-wide access to data or other assets housed in personal accounts is restricted.
Employees who resign or receive termination may retain access to cloud-based assets, but the business may lose access.
Another significant factor is that business policies and processes do not govern shadow IT. This scenario may indicate an enterprise has not backed up its cloud-based data or preserved or encoded by corporate policy.
- Increased system flaws
It complicates everything. When a company doesn’t give workers enough resources to execute their jobs and they self-provision, the company is less likely to invest in infrastructure, new skills, or procedures.
It also lacks a data source. Data analysis and reporting may be erroneous, inconsistent, or incomplete, resulting in lower data quality and compliance concerns.
- Unnecessary cost
It often helps employees cut expenditures. Long-term or business-wide adoption of such services may not be cost-effective.
A personal cloud storage service (Virtual Cloud or Hybrid Cloud) expanded to suit an enterprise account is prohibitively expensive compared to corporate-focused offerings.
Focus on your employees for a successful shadow IT strategy
Some elements you need to include within your strategy are a robust review of your IT practices, a clear vision, and a robust shadow IT policy.
But these elements are nothing without communication with your staff at every stage as you build the strategy.
After all, they are the ones the strategy is for, so they must be the focus of every decision as you build a strategy based on employee feedback and adjust the strategy per their needs.
Doing so will lead to a successful strategy that staff will follow, reducing security risks and saving resources, leading your enterprise to success.
FAQs
What is shadow IT?
Shadow IT is when employees utilize unapproved software or hardware in the workplace. The term “shadow” shows that the IT department lacks visibility into employees’ technology, making security evaluation impossible.
Staff engage in shadow IT practices without following formal IT service requests, procurement, and approval processes to bypass time constraints and policy obstacles.
Why does shadow IT exist?
Colleagues or departments frequently embrace and apply Shadow IT solutions to meet specific needs or swiftly resolve issues. Enterprises need to address shadow IT because it can cause many security breaches.
Some of the reasons shadow IT exists include:
- Needing to get tasks done faster due to rigid deadlines.
- Hybrid working resulting in less governance and policy following,
- Not having access to tools for tasks due to IT procurement issues.
- Poor communication between employees and team managers.
- Lack of understanding of security issues.
Unsanctioned applications are common in 2023 workplaces, with 41% of enterprise employees engaging in unauthorized technology practices, and knowing why staff engage in these practices can help tackle them.
What are some examples of Shadow IT?
Unsanctioned examples of Shadow IT often involve third-party software, applications, and services.
Shadow IT examples can include:
- Tools to boost productivity like Trello and Asana.
- Unapproved personal devices used on the corporate network lead to a data breach.
- Cloud storage and collaboration platforms, including Dropbox, Google Docs, Google Drive, and Microsoft OneDrive.
- Communication, collaboration tools or networking apps like Skype, Slack, WhatsApp, Zoom, Signal, and Telegram.
- Personal email accounts or a personal Dropbox account.
These cloud services and Software as a Service (SaaS) offerings often see swift adoption due to their user-friendly nature, affordability, or free accessibility.
Employees can also introduce shadow IT apps from home like generative AI tools, influenced by customer, partner, or service provider encouragement, often due to software paralysis caused by becoming overwhelmed by too many apps by their organization.
Doing so creates challenges for traditional asset management systems in detecting and monitoring devices like smartphones, laptops, USB drives, and external hard drives under Bring Your Own Device (BYOD) programs.


